
Table of Contents
New research by cybersecurity firm Kaspersky for the first half of 2020 highlights an increase in the number of cyber-attacks on ICS computers in the oil and gas and building automation industries, as the number of attacks in other industries declined.
Cyber-criminals appear to be moving their focus away from energy, automotive manufacturing and engineering, and ICS integration, but building automation systems are especially vulnerable to cyber-attacks, according to the study:
“They often have a larger attack surface than traditional ICS computers because they are frequently connected to corporate networks and the Internet. At the same time, because they traditionally belong to contractor organizations, these systems are not always managed by the organization’s corporate information security team, making them an easier target.”
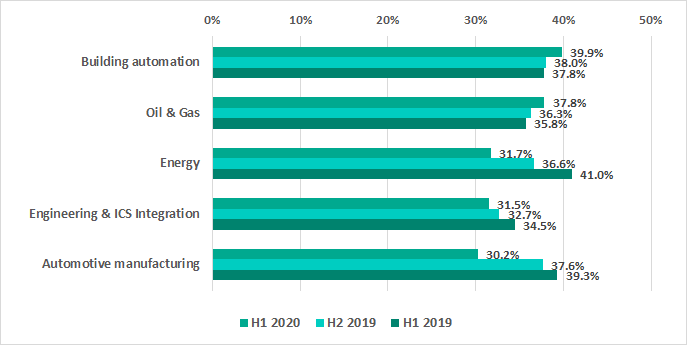
Percentage of ICS computers on which malicious objects were blocked in selected industries
“The percent of ICS computers attacked across most industries is declining, however there are still threats to specific industries that are on the rise,” said Evgeny Goncharov, security expert at Kaspersky. “The more targeted and sophisticated attacks are, the greater potential they have to cause significant damage—even if they occur less frequently. What’s more, with many enterprises forced to work remotely and sign-in to corporate systems from home, ICS have naturally become more exposed to cyberthreats. With fewer on-sight personnel, there are fewer people available to respond and mitigate an attack, meaning the consequences may be far more devastating. Given that the oil and gas and building automation infrastructures appear to be a popular target among attackers, it’s crucial that these system owners and operators take extra security precautions.”

